Difference between revisions of "HP BIOS Hacking"
m (Admin moved page BIOS Hacking to HP BIOS Hacking) |
|||
| (174 intermediate revisions by 2 users not shown) | |||
| Line 1: | Line 1: | ||
| − | + | [https://wiki.n4vx.net/index.php/Main_Page <<Back<<]<br> | |
| − | + | [[File:25L6406e.jpg|thumb|right|What a typical BIOS chip looks like]] | |
| − | Using the [https://www.sparkfun.com/products/12942 Bus Pirate] I have been successful in recovering several HP ProBook laptops that have BIOS Administrator passwords set. | + | [[File:Soic8_clip.jpg|thumb||right|Test Clip that I used]] |
| + | Using the [https://www.sparkfun.com/products/12942 Bus Pirate] I have been successful in recovering several HP EliteBook and ProBook laptops that have BIOS Administrator passwords set. After gaining access to the BIOS admin settings you can blow out all the TPM and Fingerprint stuff and reset to default security settings. Below is a rough outline of the process.<br> | ||
| + | Lets just assume that if you use any of these instructions on any of your own (or someone elses) equipment that you do so at your own demise. Kittens will die and babies will go hungry if you screw anything up. '''DO SO AT YOUR OWN RISK!!''' | ||
| + | ==Act One: Getting the Locked .bin out of the chip== | ||
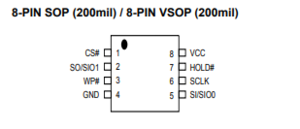
| + | [[File:MX25L6406E pins.png|thumb|right|MX25L6406E Pinout]] | ||
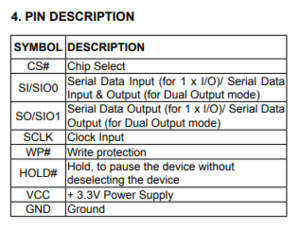
| + | [[File:MX25L6406E pin description.png|thumb|right|What the pins are...]] | ||
| + | * Gain physical access to the BIOS chip. You may find access after removing the battery or an access panel on the bottom of the laptop. Some laptops do not have easy access to the BIOS IC. On the 6470b series you have to remove the back chassis to get the test clip on the chip even though there is a tiny access window right above the chip. (I got tired of doing this and started trimming part of the plastic chassis to access it) I'm pretty sure this is for assembly line provisioning or for large IT departments that have a backprobe type setup that fits in that tiny window. | ||
| + | * Identify the manufacturer and model number of the IC. Mine was a MX25L6406E, YMMV. | ||
| + | * Obtain a datasheet for your particular IC and determine the pinout for all the necessary pins required for flashing. This is super handy for correctly identifying that you have the correct IC on the board. | ||
| + | ===My Connections=== | ||
| + | *The table below shows how a typical SPI flash chip (sitting in the center of the table) needs to be connected (NB: not all flash chips feature all of the pins below, but in general you should always connect all input pins of ICs to some defined potential (usually GND or VCC), ideally with a pull-up/down resistor in between). | ||
| − | === | + | {| style="border-collapse: collapse; border: 1px solid black;" cellpadding="5"; border="1" align="center" |
| − | + | ! Description | |
| + | ! Bus Pirate | ||
| + | ! Dir. | ||
| + | ! colspan="4"|Flash chip | ||
| + | ! Dir. | ||
| + | ! Bus Pirate | ||
| + | ! Description | ||
| + | |- | ||
| + | | align="right" | (not) Chip Select || CS || <font size="+2">→</font> || style="background: #DDDDDD;" | 1 || align="left" style="background: #DDDDDD;" | /CS || align="right" style="background: #DDDDDD;" | VCC || style="background: #DDDDDD;" | 8 || <font size="+2">←</font> || +3.3v || align="left" | Supply | ||
| + | |- | ||
| + | | align="right" | Master In, Slave Out || MISO || <font size="+2">←</font> || style="background: #DDDDDD;" | 2 || align="left" style="background: #DDDDDD;" | DO (IO1) || align="right" style="background: #DDDDDD;" | /HOLD (IO3) || style="background: #DDDDDD;" | 7 || <font size="+2">←</font> || +3.3v || align="left" | (not) hold (see datasheets) | ||
| + | |- | ||
| + | | align="right" | (not) Write Protect || +3.3v || <font size="+2">→</font> || style="background: #DDDDDD;" | 3 || align="left" style="background: #DDDDDD;" | /WP (IO2) || align="right" style="background: #DDDDDD;" | CLK || style="background: #DDDDDD;" | 6 || <font size="+2">←</font> || CLK || align="left" | The SPI clock | ||
| + | |- | ||
| + | | align="right" | Ground || GND || <font size="+2">→</font> || style="background: #DDDDDD;" | 4 || align="left" style="background: #DDDDDD;" | GND || align="right" style="background: #DDDDDD;" | DI (IO0) || style="background: #DDDDDD;" | 5 || <font size="+2">←</font> || MOSI || align="left" | Master Out, Slave In | ||
| + | |- | ||
| + | |} | ||
| + | ** Most SPI flash chips require a 3.3V supply voltage, but there exist some models that use e.g. 1.8V. Make sure the device in question is compatible before connecting any wires. <small>NB: Some rather rare SPI flash chips (e.g. Atmel AT45DB series) have a completely different layout, please beware.</small> | ||
| − | [[ProBook 6470b]]<br> | + | **Interesting findings: |
| + | ***I have found that I was able to '''''not''''' connect the Vcc or Write Protect lines on any of the pins indicated and still get a successful read and write. I let the laptop's power supply provide the proper regulated voltage. | ||
| + | ***If you use a genuine HP power supply and do not have the battery connected, it may detect the absence of the battery and disable the power supply after a few seconds. | ||
| + | ***If you use an aftermarket supply with poor voltage regulation or noise, you may experience poor consistency in your reads and SHOULD NOT flash your BIOS over SPI if this is the case. A good quality aftermarket supply may not shut off with a missing battery and allow you to read and write if you can't insert your battery due to physical chip access blocking it. | ||
| + | ===NOW, LETS DO THE THING=== | ||
| + | * Reading: The following command may work as-is: <code>$ '''flashrom -p buspirate_spi:dev=/dev/ttyUSB0,spispeed=1M -r flash.bin'''</code> | ||
| + | [[File:Flashrom -c option.png|thumb|left]] | ||
| + | *I have ran into a few models (ProBook 6470b) that had multiple SPI devices on a shared bus that were detected upon running the below command. It will quit and put you back at a prompt if it detects multiple SPI devices. If so, you may have to specify the particular chipset in the command like I did <code>$ '''flashrom -p buspirate_spi:dev=/dev/ttyUSB0,spispeed=1M -c 'MX25L6406E/MX25L6408E' -r filename.0.bin'''</code> Check the flashrom man page for details on how to do this. | ||
| + | ** You will have to define your BusPirate device <code>/dev/whatEVER</code> You can probably find this in a quick <code>dmesg</code> | ||
| + | ** You must also define your output fine <code>-r flash.bin</code> This will become important in the next step. | ||
| + | ** I never bothered trying faster SPI speeds as I was more concerned with consistent reads that speed. | ||
| + | [[File:Screenshot of BIOS read.jpg|thumb|right|I had to specify which chip out of several on the SPI bus]] | ||
| + | * Use the above command (modified with your proper device and output filename) and start the first read. You should get a moderately verbose output from flashrom indicating that it has begun the read process and it will take quite a while (sometimes over 30 minutes) to extract the binary contents of the flash IC to your specified file. Be patient!! It has not frozen or locked up. It takes quite a while. Especially if you have a larger BIOS file size. | ||
| + | * If the read was successful, change the output filename, something like <code>flash.1.bin</code> and do it again. | ||
| + | <code>$ '''flashrom -p buspirate_spi:dev=/dev/ttyUSB0,spispeed=1M -r flash.1.bin'''</code> | ||
| + | ===Verify the integrity of your MULTIPLE reads=== | ||
| + | * Now, you should have two identical binary files if your reads were valid. Let's check the integrity of the two files against each other. | ||
| + | <code>$ '''md5sum ./*.bin'''</code> | ||
| + | *This command should indicate a md5 checksum for the two files that is IDENTICAL. If the checksum is identical, it means that you have read two perfect copies of the IC's contents with no errors. | ||
| + | * Just for good measure, do a third read with a new file name <code>flash.2.bin</code> and repeat the <code>md5sum</code> check to make sure you have three (3) identical files. | ||
| + | [[File:BIOS md5sum x3 good.png|thumb|left]] | ||
| + | * '''If you cannot get consistent reads.... DO NOT EVER WRITE!! You have been warned. My suggestion is to make sure you can get, at a minimum, THREE full binary reads that have the same checksum. If you cannot do this, you may have to resort to supplying the proper Vcc to the chip externally with proper regulation. DO SO AT YOUR OWN RISK.''' | ||
| + | [[File:BIOS work in action.jpg|thumb|right|Clippy go brrrrr]] | ||
| + | <br><br> | ||
| + | ---- | ||
| − | [ | + | ==Act Two: The actual h4x0ring of the thing== |
| + | You now have three identical copies of the binary file that lives inside your target machine's BIOS IC. Now what? If you don't have three copies and still want to continue without making sure you have a pure copy, you are a true savage. Live your life. Now, here comes the fun part. It's almost like finding a needle in a hay stack. Except it doesn't look like a needle. It looks like this <code>´�ÌÆ¢6@B!6@A!�L|ªœ�D�p†�Ã�q82].2‰D</code>. Fortunately someone much smarter and more talented than me has already figured out where the important bits lie. Let's walk thru this. | ||
| + | ===Open the file in a hex editor=== | ||
| + | *I like using <code>HxD</code> or <code>wxHexEditor</code> or <code>Bless Hex Editor</code> or <code>okteta</code>in linux. Any of them will get you thru this process. <br> | ||
| + | *You will be looking for a block of text (mine was about 80% down in the file) that will be something like <code>B.I.O.S...A.d.m.i.n.i.s.t.r.a.t.o.r</code> followed by three null bytes <code>00 00 00</code> and then a lot of jibberish until a three byte delimiter. ''Look for what you think is the delimiter bytes and search the file to make sure those 3 bytes show up in lots of places in the file. It should be obvious if you find the right one.'' | ||
| + | *'''Make everything null <code>00 00 00 00</code>from the three null bytes <code>00 00 00</code> to the <code>AA 55 7F</code>''' (or whatever you find as the delimiter)<br> | ||
| + | <strong>Before</strong> | ||
| + | <small><code>006C:5560 | 00 00 00 00 00 00 00 00 01 55 AA 00 00 {{ font bg|#00F000|AA 55 7F}} | .........Uª..ªU. | ||
| + | 006C:5570 | {{ font bg|#B0B0F0|00 07 00 00 00 00 00 00 00 00 00 00 00 FF FF FF}} | {{ font bg|#B0B0F0|.............ÿÿÿ}} | ||
| + | 006C:5580 | {{ font bg|#B0B0F0|FF FF FF FF FF FF FF FF FF FF FF FF FF 00 00 00}} | {{ font bg|#B0B0F0|ÿÿÿÿÿÿÿÿÿÿÿÿÿ...}} | ||
| + | 006C:5590 | {{ font bg|#B0B0F0|00 1C 00 00 00 57 00 00 00 66 9D C5 29 B4 F2 5E}} | {{ font bg|#B0B0F0|.....W...f.Å)´ò^}} | ||
| + | 006C:55A0 | {{ font bg|#B0B0F0|43 9A 75 E5 E6 E4 97 3C 22 48 00 50 00 5F 00 42}} | {{ font bg|#B0B0F0|C.uåæä.<"H.P._.B}} | ||
| + | 006C:55B0 | {{ font bg|#B0B0F0|00 69 00 6F 00 73 00 55 00 73 00 65 00 72 00 30}} | {{ font bg|#B0B0F0|.i.o.s.U.s.e.r.0}} | ||
| + | 006C:55C0 | {{ font bg|#B0B0F0|00 30 00 00 00 42 00 49 00 4F 00 53 00 20 00 41}} | {{ font bg|#B0B0F0|.0...B.I.O.S. .A}} | ||
| + | 006C:55D0 | {{ font bg|#B0B0F0|00 64 00 6D 00 69 00 6E 00 69 00 73 00 74 00 72}} | {{ font bg|#B0B0F0|.d.m.i.n.i.s.t.r}} | ||
| + | 006C:55E0 | {{ font bg|#B0B0F0|00 61 00 74 00 6F 00 72}} {{font bg|#FFF68F|00 00 00}} {{ font bg|#F0B0B0|00 00 00 00 00}} | {{ font bg|#B0B0F0|.a.t.o.r}}{{ font bg|#FFF68F|...}}{{ font bg|#F0B0B0|.....}} <-- MAKE ALL THESE HEX VALUES SHADED IN RED '''00''' | ||
| + | 006C:55F0 | {{ font bg|#F0B0B0|00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00}} | {{ font bg|#F0B0B0|................}} <-- MAKE ALL THESE HEX VALUES SHADED IN RED '''00''' | ||
| + | 006C:5600 | {{ font bg|#F0B0B0|00 00 00 00 00 00 00 EC 1A 54 92 FB 06 34 60 E4}} | {{ font bg|#F0B0B0|.......ì.T.û.4`ä}} <-- MAKE ALL THESE HEX VALUES SHADED IN RED '''00''' | ||
| + | 006C:5610 | {{ font bg|#F0B0B0|26 59 99 64 EB 61 4D 04 0D 3D C0 01}} {{ font bg|#00F000|AA 55 7F}} {{ font bg|#B0B0F0|00}} | {{ font bg|#F0B0B0|<nowiki>&Y.dëaM..=À.</nowiki>}}{{ font bg|#00F000|ªU.}}{{ font bg|#B0B0F0|.}} <-- MAKE ALL THESE HEX VALUES SHADED IN RED '''00''' | ||
| + | 006C:5620 | {{ font bg|#B0B0F0|07 00 00 00 00 00 00 00 00 00 00 00 FF FF FF FF}} | {{ font bg|#B0B0F0|............ÿÿÿÿ}} | ||
| + | 006C:5630 | {{ font bg|#B0B0F0|FF FF FF FF FF FF FF FF FF FF FF FF 00 00 00 00}} | {{ font bg|#B0B0F0|ÿÿÿÿÿÿÿÿÿÿÿÿ....}} | ||
| + | 006C:5640 | {{ font bg|#B0B0F0|2A 00 00 00 14 00 00 00 66 9D C5 29 B4 F2 5E 43}} | {{ font bg|#B0B0F0|*.......f.Å)´ò^C}} | ||
| + | 006C:5650 | {{ font bg|#B0B0F0|9A 75 E5 E6 E4 97 3C 22 48 00 50 00 5F 00 42 00}} | {{ font bg|#B0B0F0|.uåæä.<"H.P._.B.}} | ||
| + | 006C:5660 | {{ font bg|#B0B0F0|49 00 4F 00 53 00 41 00 64 00 6D 00 69 00 6E 00}} | {{ font bg|#B0B0F0|I.O.S.A.d.m.i.n.}} | ||
| + | 006C:5670 | {{ font bg|#B0B0F0|53 00 63 00 61 00 6E 00 43 00 6F 00 64 00 65}} {{font bg|#FFF68F|00}} | {{ font bg|#B0B0F0|S.c.a.n.C.o.d.e}}{{ font bg|#FFF68F|.}} | ||
| + | 006C:5680 | {{font bg|#FFF68F|00 00}} {{ font bg|#F0B0B0|F4 E7 1B C9 56 4D D4 82 1D 84 58 4F 39 4C}} | {{ font bg|#FFF68F|..}}{{ font bg|#F0B0B0|ôç.ÉVMÔ...XO9L}} <-- MAKE ALL THESE HEX VALUES SHADED IN RED '''00''' | ||
| + | 006C:5690 | {{ font bg|#F0B0B0|A7 27 3E BC DA D9}} {{ font bg|#00F000|AA 55 7F}} 00 07 00 00 00 00 00 | {{ font bg|#F0B0B0|§'>¼ÚÙ}}{{ font bg|#00F000|ªU.}}....... <-- MAKE ALL THESE HEX VALUES SHADED IN RED '''00''' | ||
| + | 006C:56A0 | 00 00 00 00 00 00 FF FF FF FF FF FF FF FF FF FF | ......ÿÿÿÿÿÿÿÿÿÿ | ||
| + | 006C:56B0 | FF FF FF FF FF FF 00 00 00 00 2A 00 00 00 4C 00 | ÿÿÿÿÿÿ....*...L. | ||
| + | 006C:56C0 | 00 00 43 0D 09 14 E6 63 A6 4A 82 69 DF 5B 8B 8C | ..C...æc¦J.iß[..</code><br></small> | ||
| + | <strong>After</strong> | ||
| + | <small><code>006C:5560 | 00 00 00 00 00 00 00 00 01 55 AA 00 00 {{ font bg|#00F000|AA 55 7F}} | .........Uª..ªU. | ||
| + | 006C:5570 | {{ font bg|#B0B0F0|00 07 00 00 00 00 00 00 00 00 00 00 00 FF FF FF}} | {{ font bg|#B0B0F0|.............ÿÿÿ}} | ||
| + | 006C:5580 | {{ font bg|#B0B0F0|FF FF FF FF FF FF FF FF FF FF FF FF FF 00 00 00}} | {{ font bg|#B0B0F0|ÿÿÿÿÿÿÿÿÿÿÿÿÿ...}} | ||
| + | 006C:5590 | {{ font bg|#B0B0F0|00 1C 00 00 00 57 00 00 00 66 9D C5 29 B4 F2 5E}} | {{ font bg|#B0B0F0|.....W...f.Å)´ò^}} | ||
| + | 006C:55A0 | {{ font bg|#B0B0F0|43 9A 75 E5 E6 E4 97 3C 22 48 00 50 00 5F 00 42}} | {{ font bg|#B0B0F0|C.uåæä.<"H.P._.B}} | ||
| + | 006C:55B0 | {{ font bg|#B0B0F0|00 69 00 6F 00 73 00 55 00 73 00 65 00 72 00 30}} | {{ font bg|#B0B0F0|.i.o.s.U.s.e.r.0}} | ||
| + | 006C:55C0 | {{ font bg|#B0B0F0|00 30 00 00 00 42 00 49 00 4F 00 53 00 20 00 41}} | {{ font bg|#B0B0F0|.0...B.I.O.S. .A}} | ||
| + | 006C:55D0 | {{ font bg|#B0B0F0|00 64 00 6D 00 69 00 6E 00 69 00 73 00 74 00 72}} | {{ font bg|#B0B0F0|.d.m.i.n.i.s.t.r}} | ||
| + | 006C:55E0 | {{ font bg|#B0B0F0|00 61 00 74 00 6F 00 72}} {{font bg|#FFF68F|00 00 00}} {{ font bg|#F0B0B0|00 00 00 00 00}} | {{ font bg|#B0B0F0|.a.t.o.r}}{{ font bg|#FFF68F|...}}{{ font bg|#F0B0B0|.....}} <-- LIKE THIS | ||
| + | 006C:55F0 | {{ font bg|#F0B0B0|00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00}} | {{ font bg|#F0B0B0|................}} <-- LIKE THIS | ||
| + | 006C:5600 | {{ font bg|#F0B0B0|00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00}} | {{ font bg|#F0B0B0|................}} <-- LIKE THIS | ||
| + | 006C:5610 | {{ font bg|#F0B0B0|00 00 00 00 00 00 00 00 00 00 00 00}} {{ font bg|#00F000|AA 55 7F}} {{ font bg|#B0B0F0|00}} | {{ font bg|#F0B0B0|............}}{{ font bg|#00F000|ªU.}}{{ font bg|#B0B0F0|.}} <-- LIKE THIS | ||
| + | 006C:5620 | {{ font bg|#B0B0F0|07 00 00 00 00 00 00 00 00 00 00 00 FF FF FF FF}} | {{ font bg|#B0B0F0|............ÿÿÿÿ}} | ||
| + | 006C:5630 | {{ font bg|#B0B0F0|FF FF FF FF FF FF FF FF FF FF FF FF 00 00 00 00}} | {{ font bg|#B0B0F0|ÿÿÿÿÿÿÿÿÿÿÿÿ....}} | ||
| + | 006C:5640 | {{ font bg|#B0B0F0|2A 00 00 00 14 00 00 00 66 9D C5 29 B4 F2 5E 43}} | {{ font bg|#B0B0F0|*.......f.Å)´ò^C}} | ||
| + | 006C:5650 | {{ font bg|#B0B0F0|9A 75 E5 E6 E4 97 3C 22 48 00 50 00 5F 00 42 00}} | {{ font bg|#B0B0F0|.uåæä.<"H.P._.B.}} | ||
| + | 006C:5660 | {{ font bg|#B0B0F0|49 00 4F 00 53 00 41 00 64 00 6D 00 69 00 6E 00}} | {{ font bg|#B0B0F0|I.O.S.A.d.m.i.n.}} | ||
| + | 006C:5670 | {{ font bg|#B0B0F0|53 00 63 00 61 00 6E 00 43 00 6F 00 64 00 65}} {{font bg|#FFF68F|00}} | {{ font bg|#B0B0F0|S.c.a.n.C.o.d.e}}{{ font bg|#FFF68F|.}} | ||
| + | 006C:5680 | {{font bg|#FFF68F|00 00}} {{ font bg|#F0B0B0|00 00 00 00 00 00 00 00 00 00 00 00 00 00}} | {{ font bg|#FFF68F|..}}{{ font bg|#F0B0B0|..............}} <-- LIKE THIS | ||
| + | 006C:5690 | {{ font bg|#F0B0B0|00 00 00 00 00 00}} {{ font bg|#00F000|AA 55 7F}} 00 07 00 00 00 00 00 | {{ font bg|#F0B0B0|......}}{{ font bg|#00F000|ªU.}}....... <-- LIKE THIS | ||
| + | 006C:56A0 | 00 00 00 00 00 00 FF FF FF FF FF FF FF FF FF FF | ......ÿÿÿÿÿÿÿÿÿÿ | ||
| + | 006C:56B0 | FF FF FF FF FF FF 00 00 00 00 2A 00 00 00 4C 00 | ÿÿÿÿÿÿ....*...L. | ||
| + | 006C:56C0 | 00 00 43 0D 09 14 E6 63 A6 4A 82 69 DF 5B 8B 8C | ..C...æc¦J.iß</code></small> | ||
| − | === Sources === | + | *<strong>'''When you are done with the editing, save the file as your "No Password" file (i.e. <code>file.nopw.bin</code>)'''</strong> |
| + | *You can now put on your black hoodie and Guy Fawkes mask as you are officially now a hacker. | ||
| + | |||
| + | ==Act Three: Put the cat back in the bag== | ||
| + | [[File:Binwalk diff.png|thumb|right|Binwalk diff]] | ||
| + | *Compare your changes in the file with <code>binwalk -Wi file.0.bin file.nopw.bin</code> to doublecheck that you didn't mess up any other lines than the ones you intended to edit. | ||
| + | *If you are confident that you have made the correct changes and are ready to proceed on writing the modified binary, take a deep breath and proceed. | ||
| + | ====Write==== | ||
| + | *Time to stuff this cat back into the burlap sack. | ||
| + | ** Type in the following command and go take a nap: <code>flashrom -p buspirate_spi:dev=/dev/ttyUSB0,spispeed=1M -w file.nopw.bin</code> | ||
| + | **Use the appropriate device (<code>/dev/whatEVER</code>) and filename (<code>file.nopw.bin</code>) | ||
| + | **It will check out the target chip, write and then verify the binary. Get a snack and take a hike while you wait. It could take a full 45 mins to an hour. Especially if you have one of those fancy 25L128xxxx dudes. [[File:Flashrom writing.png|thumb|right|Flashrom writing]] | ||
| + | **If you get the following message, you are 90% there my dude! | ||
| + | <code>Reading old flash chip contents... done. | ||
| + | Erasing and writing flash chip... Erase/write done. | ||
| + | Verifying flash... VERIFIED.</code> | ||
| + | *Have a drink and get ready to enjoy your unlocked BIOS!! | ||
| + | |||
| + | ==Act Four: Clean up after surgery== | ||
| + | Hopefully not much blood. '''more info coming soon ''These steps are from memory. Exact steps to be published when I feel like it.''''' | ||
| + | There are still a few steps to fully resurrect the h4X0rzd BIOS to it's default state. <br> | ||
| + | '''Basically...'''<br> | ||
| + | #Just mash enter when it asks for BIOS Admin password | ||
| + | #Change password, reboot | ||
| + | #Change password to a blank entry (dont put in a password), reboot | ||
| + | #You might have a fully clean BIOS and can reset TPM and factory BIOS defaults. | ||
| + | #If not, set a new password, reboot, set no password, reboot and check again. | ||
| + | |||
| + | I will elaborate in detail eventually.. or not. | ||
| + | ---- | ||
| + | bottomtext | ||
| + | |||
| + | ==Errata== | ||
| + | I hope to start a small library of BIOS binaries for the models I have recovered and the procedure used to recover a locked system. | ||
| + | |||
| + | == HP ProBook & EliteBook == | ||
| + | *[[EliteBook Revolve 810]] | ||
| + | *[[ProBook 6470b]] | ||
| + | *[[ProBook 6560b]] | ||
| + | |||
| + | === Information Sources === | ||
* [https://gracefulsecurity.com/extracting-flash-memory-over-spi/ General info about pinouts and flashrom] | * [https://gracefulsecurity.com/extracting-flash-memory-over-spi/ General info about pinouts and flashrom] | ||
* [https://flashrom.org/Bus_Pirate Official flashrom Bus Pirate wiki] | * [https://flashrom.org/Bus_Pirate Official flashrom Bus Pirate wiki] | ||
* [https://www.systutorials.com/docs/linux/man/8-flashrom/ flashrom man page](I guess no women allowed) | * [https://www.systutorials.com/docs/linux/man/8-flashrom/ flashrom man page](I guess no women allowed) | ||
Latest revision as of 20:41, 3 May 2022
Using the Bus Pirate I have been successful in recovering several HP EliteBook and ProBook laptops that have BIOS Administrator passwords set. After gaining access to the BIOS admin settings you can blow out all the TPM and Fingerprint stuff and reset to default security settings. Below is a rough outline of the process.
Lets just assume that if you use any of these instructions on any of your own (or someone elses) equipment that you do so at your own demise. Kittens will die and babies will go hungry if you screw anything up. DO SO AT YOUR OWN RISK!!
Act One: Getting the Locked .bin out of the chip
- Gain physical access to the BIOS chip. You may find access after removing the battery or an access panel on the bottom of the laptop. Some laptops do not have easy access to the BIOS IC. On the 6470b series you have to remove the back chassis to get the test clip on the chip even though there is a tiny access window right above the chip. (I got tired of doing this and started trimming part of the plastic chassis to access it) I'm pretty sure this is for assembly line provisioning or for large IT departments that have a backprobe type setup that fits in that tiny window.
- Identify the manufacturer and model number of the IC. Mine was a MX25L6406E, YMMV.
- Obtain a datasheet for your particular IC and determine the pinout for all the necessary pins required for flashing. This is super handy for correctly identifying that you have the correct IC on the board.
My Connections
- The table below shows how a typical SPI flash chip (sitting in the center of the table) needs to be connected (NB: not all flash chips feature all of the pins below, but in general you should always connect all input pins of ICs to some defined potential (usually GND or VCC), ideally with a pull-up/down resistor in between).
| Description | Bus Pirate | Dir. | Flash chip | Dir. | Bus Pirate | Description | |||
|---|---|---|---|---|---|---|---|---|---|
| (not) Chip Select | CS | → | 1 | /CS | VCC | 8 | ← | +3.3v | Supply |
| Master In, Slave Out | MISO | ← | 2 | DO (IO1) | /HOLD (IO3) | 7 | ← | +3.3v | (not) hold (see datasheets) |
| (not) Write Protect | +3.3v | → | 3 | /WP (IO2) | CLK | 6 | ← | CLK | The SPI clock |
| Ground | GND | → | 4 | GND | DI (IO0) | 5 | ← | MOSI | Master Out, Slave In |
- Most SPI flash chips require a 3.3V supply voltage, but there exist some models that use e.g. 1.8V. Make sure the device in question is compatible before connecting any wires. NB: Some rather rare SPI flash chips (e.g. Atmel AT45DB series) have a completely different layout, please beware.
- Interesting findings:
- I have found that I was able to not connect the Vcc or Write Protect lines on any of the pins indicated and still get a successful read and write. I let the laptop's power supply provide the proper regulated voltage.
- If you use a genuine HP power supply and do not have the battery connected, it may detect the absence of the battery and disable the power supply after a few seconds.
- If you use an aftermarket supply with poor voltage regulation or noise, you may experience poor consistency in your reads and SHOULD NOT flash your BIOS over SPI if this is the case. A good quality aftermarket supply may not shut off with a missing battery and allow you to read and write if you can't insert your battery due to physical chip access blocking it.
- Interesting findings:
NOW, LETS DO THE THING
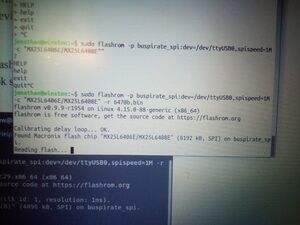
- Reading: The following command may work as-is:
$ flashrom -p buspirate_spi:dev=/dev/ttyUSB0,spispeed=1M -r flash.bin
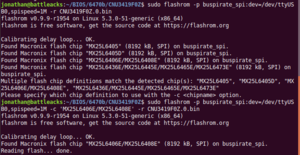
- I have ran into a few models (ProBook 6470b) that had multiple SPI devices on a shared bus that were detected upon running the below command. It will quit and put you back at a prompt if it detects multiple SPI devices. If so, you may have to specify the particular chipset in the command like I did
$ flashrom -p buspirate_spi:dev=/dev/ttyUSB0,spispeed=1M -c 'MX25L6406E/MX25L6408E' -r filename.0.binCheck the flashrom man page for details on how to do this.- You will have to define your BusPirate device
/dev/whatEVERYou can probably find this in a quickdmesg - You must also define your output fine
-r flash.binThis will become important in the next step. - I never bothered trying faster SPI speeds as I was more concerned with consistent reads that speed.
- You will have to define your BusPirate device
- Use the above command (modified with your proper device and output filename) and start the first read. You should get a moderately verbose output from flashrom indicating that it has begun the read process and it will take quite a while (sometimes over 30 minutes) to extract the binary contents of the flash IC to your specified file. Be patient!! It has not frozen or locked up. It takes quite a while. Especially if you have a larger BIOS file size.
- If the read was successful, change the output filename, something like
flash.1.binand do it again.
$ flashrom -p buspirate_spi:dev=/dev/ttyUSB0,spispeed=1M -r flash.1.bin
Verify the integrity of your MULTIPLE reads
- Now, you should have two identical binary files if your reads were valid. Let's check the integrity of the two files against each other.
$ md5sum ./*.bin
- This command should indicate a md5 checksum for the two files that is IDENTICAL. If the checksum is identical, it means that you have read two perfect copies of the IC's contents with no errors.
- Just for good measure, do a third read with a new file name
flash.2.binand repeat themd5sumcheck to make sure you have three (3) identical files.
- If you cannot get consistent reads.... DO NOT EVER WRITE!! You have been warned. My suggestion is to make sure you can get, at a minimum, THREE full binary reads that have the same checksum. If you cannot do this, you may have to resort to supplying the proper Vcc to the chip externally with proper regulation. DO SO AT YOUR OWN RISK.
Act Two: The actual h4x0ring of the thing
You now have three identical copies of the binary file that lives inside your target machine's BIOS IC. Now what? If you don't have three copies and still want to continue without making sure you have a pure copy, you are a true savage. Live your life. Now, here comes the fun part. It's almost like finding a needle in a hay stack. Except it doesn't look like a needle. It looks like this ´�ÌÆ¢6@B!6@A!�L|ªœ�D�p†�Ã�q82].2‰D. Fortunately someone much smarter and more talented than me has already figured out where the important bits lie. Let's walk thru this.
Open the file in a hex editor
- I like using
HxDorwxHexEditororBless Hex Editororoktetain linux. Any of them will get you thru this process. - You will be looking for a block of text (mine was about 80% down in the file) that will be something like
B.I.O.S...A.d.m.i.n.i.s.t.r.a.t.o.rfollowed by three null bytes00 00 00and then a lot of jibberish until a three byte delimiter. Look for what you think is the delimiter bytes and search the file to make sure those 3 bytes show up in lots of places in the file. It should be obvious if you find the right one. - Make everything null
00 00 00 00from the three null bytes00 00 00to theAA 55 7F(or whatever you find as the delimiter)
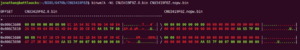
Before
006C:5560 | 00 00 00 00 00 00 00 00 01 55 AA 00 00 AA 55 7F | .........Uª..ªU. 006C:5570 | 00 07 00 00 00 00 00 00 00 00 00 00 00 FF FF FF | .............ÿÿÿ 006C:5580 | FF FF FF FF FF FF FF FF FF FF FF FF FF 00 00 00 | ÿÿÿÿÿÿÿÿÿÿÿÿÿ... 006C:5590 | 00 1C 00 00 00 57 00 00 00 66 9D C5 29 B4 F2 5E | .....W...f.Å)´ò^ 006C:55A0 | 43 9A 75 E5 E6 E4 97 3C 22 48 00 50 00 5F 00 42 | C.uåæä.<"H.P._.B 006C:55B0 | 00 69 00 6F 00 73 00 55 00 73 00 65 00 72 00 30 | .i.o.s.U.s.e.r.0 006C:55C0 | 00 30 00 00 00 42 00 49 00 4F 00 53 00 20 00 41 | .0...B.I.O.S. .A 006C:55D0 | 00 64 00 6D 00 69 00 6E 00 69 00 73 00 74 00 72 | .d.m.i.n.i.s.t.r 006C:55E0 | 00 61 00 74 00 6F 00 72 00 00 00 00 00 00 00 00 | .a.t.o.r........ <-- MAKE ALL THESE HEX VALUES SHADED IN RED 00 006C:55F0 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | ................ <-- MAKE ALL THESE HEX VALUES SHADED IN RED 00 006C:5600 | 00 00 00 00 00 00 00 EC 1A 54 92 FB 06 34 60 E4 | .......ì.T.û.4`ä <-- MAKE ALL THESE HEX VALUES SHADED IN RED 00 006C:5610 | 26 59 99 64 EB 61 4D 04 0D 3D C0 01 AA 55 7F 00 | &Y.dëaM..=À.ªU.. <-- MAKE ALL THESE HEX VALUES SHADED IN RED 00 006C:5620 | 07 00 00 00 00 00 00 00 00 00 00 00 FF FF FF FF | ............ÿÿÿÿ 006C:5630 | FF FF FF FF FF FF FF FF FF FF FF FF 00 00 00 00 | ÿÿÿÿÿÿÿÿÿÿÿÿ.... 006C:5640 | 2A 00 00 00 14 00 00 00 66 9D C5 29 B4 F2 5E 43 | *.......f.Å)´ò^C 006C:5650 | 9A 75 E5 E6 E4 97 3C 22 48 00 50 00 5F 00 42 00 | .uåæä.<"H.P._.B. 006C:5660 | 49 00 4F 00 53 00 41 00 64 00 6D 00 69 00 6E 00 | I.O.S.A.d.m.i.n. 006C:5670 | 53 00 63 00 61 00 6E 00 43 00 6F 00 64 00 65 00 | S.c.a.n.C.o.d.e. 006C:5680 | 00 00 F4 E7 1B C9 56 4D D4 82 1D 84 58 4F 39 4C | ..ôç.ÉVMÔ...XO9L <-- MAKE ALL THESE HEX VALUES SHADED IN RED 00 006C:5690 | A7 27 3E BC DA D9 AA 55 7F 00 07 00 00 00 00 00 | §'>¼ÚÙªU........ <-- MAKE ALL THESE HEX VALUES SHADED IN RED 00 006C:56A0 | 00 00 00 00 00 00 FF FF FF FF FF FF FF FF FF FF | ......ÿÿÿÿÿÿÿÿÿÿ 006C:56B0 | FF FF FF FF FF FF 00 00 00 00 2A 00 00 00 4C 00 | ÿÿÿÿÿÿ....*...L. 006C:56C0 | 00 00 43 0D 09 14 E6 63 A6 4A 82 69 DF 5B 8B 8C | ..C...æc¦J.iß[..
After
006C:5560 | 00 00 00 00 00 00 00 00 01 55 AA 00 00 AA 55 7F | .........Uª..ªU.
006C:5570 | 00 07 00 00 00 00 00 00 00 00 00 00 00 FF FF FF | .............ÿÿÿ
006C:5580 | FF FF FF FF FF FF FF FF FF FF FF FF FF 00 00 00 | ÿÿÿÿÿÿÿÿÿÿÿÿÿ...
006C:5590 | 00 1C 00 00 00 57 00 00 00 66 9D C5 29 B4 F2 5E | .....W...f.Å)´ò^
006C:55A0 | 43 9A 75 E5 E6 E4 97 3C 22 48 00 50 00 5F 00 42 | C.uåæä.<"H.P._.B
006C:55B0 | 00 69 00 6F 00 73 00 55 00 73 00 65 00 72 00 30 | .i.o.s.U.s.e.r.0
006C:55C0 | 00 30 00 00 00 42 00 49 00 4F 00 53 00 20 00 41 | .0...B.I.O.S. .A
006C:55D0 | 00 64 00 6D 00 69 00 6E 00 69 00 73 00 74 00 72 | .d.m.i.n.i.s.t.r
006C:55E0 | 00 61 00 74 00 6F 00 72 00 00 00 00 00 00 00 00 | .a.t.o.r........ <-- LIKE THIS
006C:55F0 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | ................ <-- LIKE THIS
006C:5600 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | ................ <-- LIKE THIS
006C:5610 | 00 00 00 00 00 00 00 00 00 00 00 00 AA 55 7F 00 | ............ªU.. <-- LIKE THIS
006C:5620 | 07 00 00 00 00 00 00 00 00 00 00 00 FF FF FF FF | ............ÿÿÿÿ
006C:5630 | FF FF FF FF FF FF FF FF FF FF FF FF 00 00 00 00 | ÿÿÿÿÿÿÿÿÿÿÿÿ....
006C:5640 | 2A 00 00 00 14 00 00 00 66 9D C5 29 B4 F2 5E 43 | *.......f.Å)´ò^C
006C:5650 | 9A 75 E5 E6 E4 97 3C 22 48 00 50 00 5F 00 42 00 | .uåæä.<"H.P._.B.
006C:5660 | 49 00 4F 00 53 00 41 00 64 00 6D 00 69 00 6E 00 | I.O.S.A.d.m.i.n.
006C:5670 | 53 00 63 00 61 00 6E 00 43 00 6F 00 64 00 65 00 | S.c.a.n.C.o.d.e.
006C:5680 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | ................ <-- LIKE THIS
006C:5690 | 00 00 00 00 00 00 AA 55 7F 00 07 00 00 00 00 00 | ......ªU........ <-- LIKE THIS
006C:56A0 | 00 00 00 00 00 00 FF FF FF FF FF FF FF FF FF FF | ......ÿÿÿÿÿÿÿÿÿÿ
006C:56B0 | FF FF FF FF FF FF 00 00 00 00 2A 00 00 00 4C 00 | ÿÿÿÿÿÿ....*...L.
006C:56C0 | 00 00 43 0D 09 14 E6 63 A6 4A 82 69 DF 5B 8B 8C | ..C...æc¦J.iß
- When you are done with the editing, save the file as your "No Password" file (i.e.
file.nopw.bin) - You can now put on your black hoodie and Guy Fawkes mask as you are officially now a hacker.
Act Three: Put the cat back in the bag
- Compare your changes in the file with
binwalk -Wi file.0.bin file.nopw.binto doublecheck that you didn't mess up any other lines than the ones you intended to edit. - If you are confident that you have made the correct changes and are ready to proceed on writing the modified binary, take a deep breath and proceed.
Write
- Time to stuff this cat back into the burlap sack.
- Type in the following command and go take a nap:
flashrom -p buspirate_spi:dev=/dev/ttyUSB0,spispeed=1M -w file.nopw.bin - Use the appropriate device (
/dev/whatEVER) and filename (file.nopw.bin) - It will check out the target chip, write and then verify the binary. Get a snack and take a hike while you wait. It could take a full 45 mins to an hour. Especially if you have one of those fancy 25L128xxxx dudes.
- If you get the following message, you are 90% there my dude!
- Type in the following command and go take a nap:
Reading old flash chip contents... done.
Erasing and writing flash chip... Erase/write done.
Verifying flash... VERIFIED.
- Have a drink and get ready to enjoy your unlocked BIOS!!
Act Four: Clean up after surgery
Hopefully not much blood. more info coming soon These steps are from memory. Exact steps to be published when I feel like it.
There are still a few steps to fully resurrect the h4X0rzd BIOS to it's default state.
Basically...
- Just mash enter when it asks for BIOS Admin password
- Change password, reboot
- Change password to a blank entry (dont put in a password), reboot
- You might have a fully clean BIOS and can reset TPM and factory BIOS defaults.
- If not, set a new password, reboot, set no password, reboot and check again.
I will elaborate in detail eventually.. or not.
bottomtext
Errata
I hope to start a small library of BIOS binaries for the models I have recovered and the procedure used to recover a locked system.
HP ProBook & EliteBook
Information Sources
- General info about pinouts and flashrom
- Official flashrom Bus Pirate wiki
- flashrom man page(I guess no women allowed)